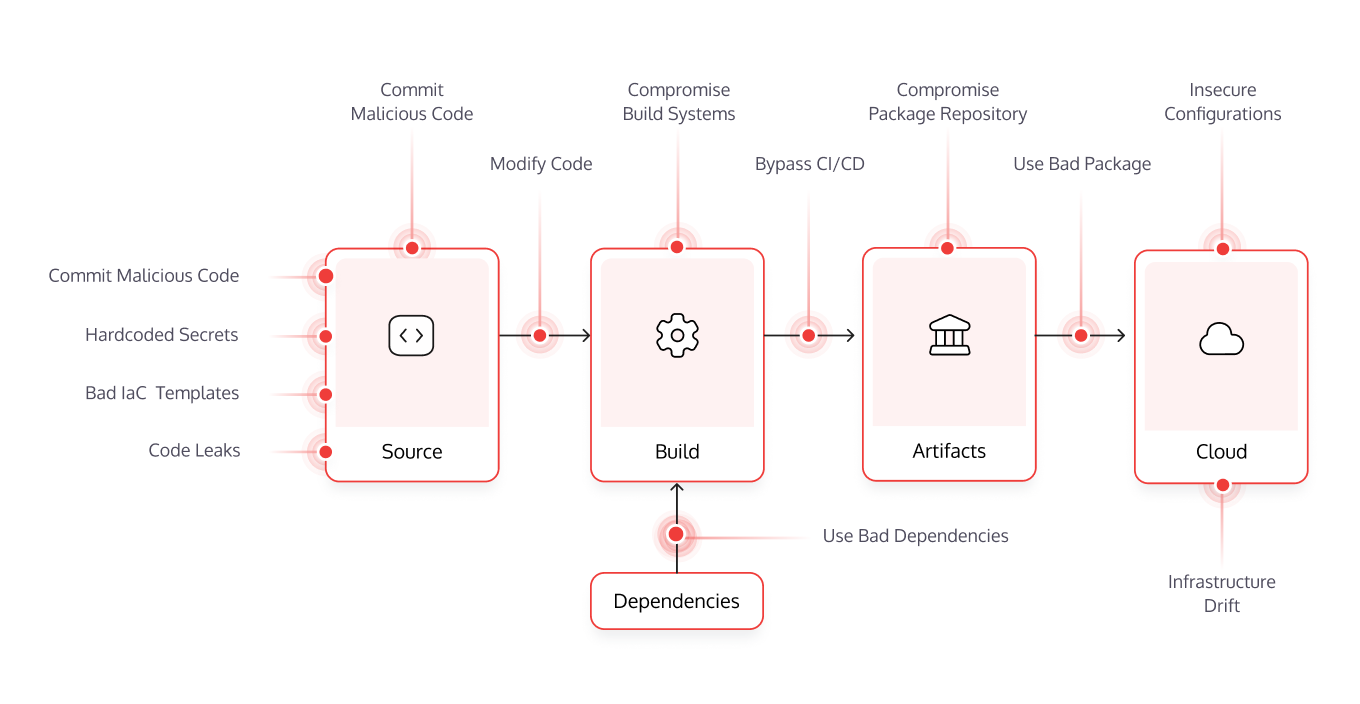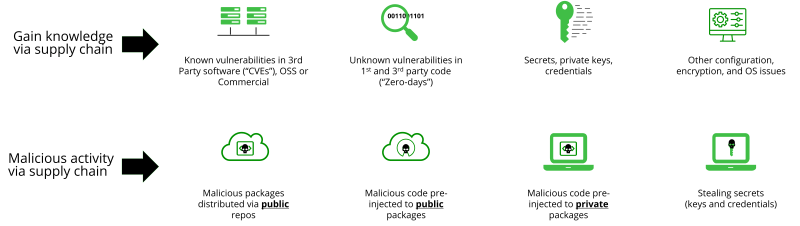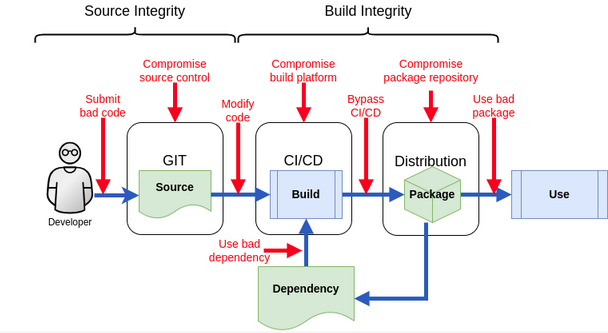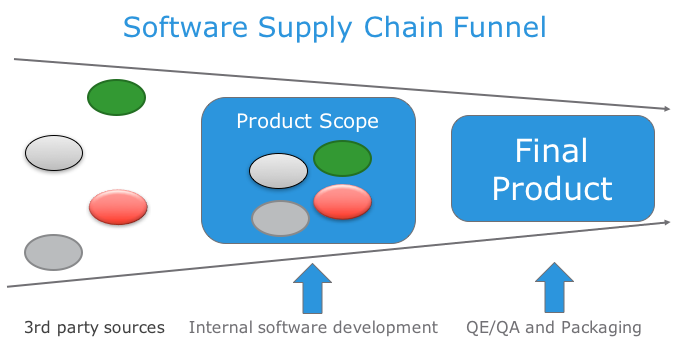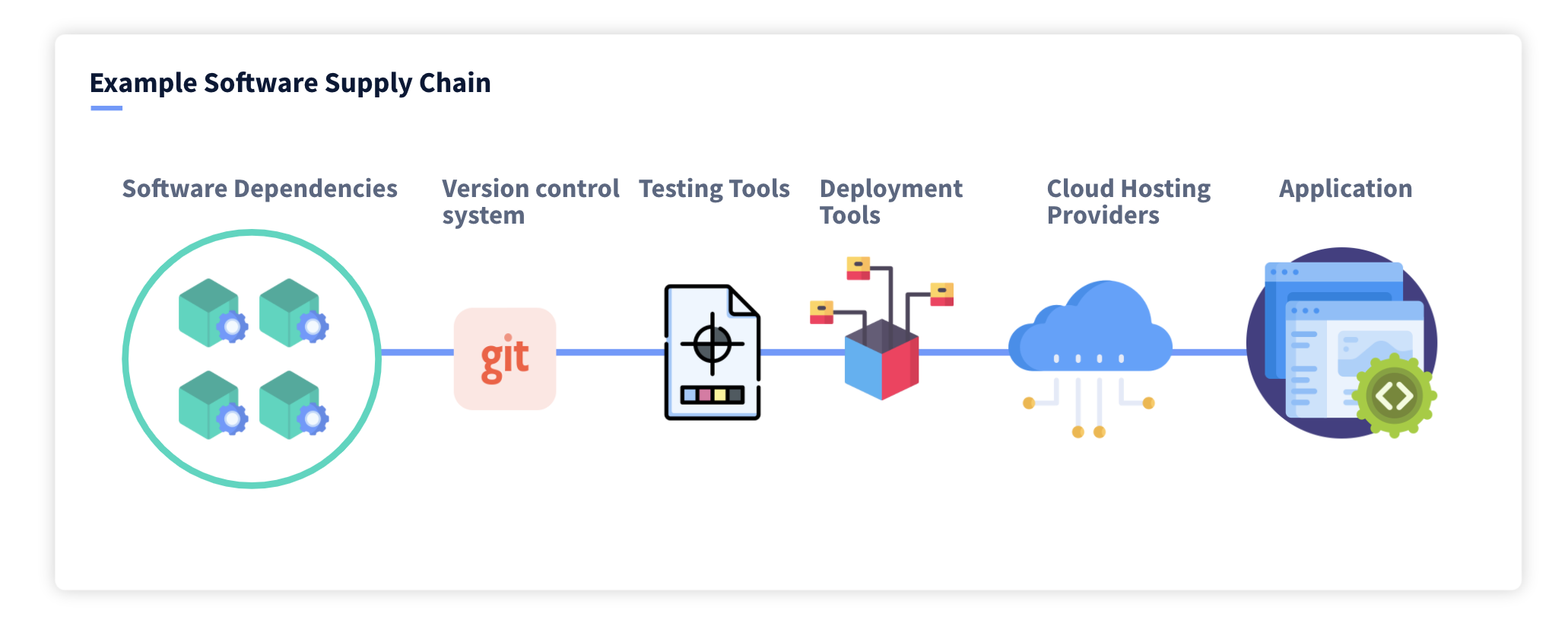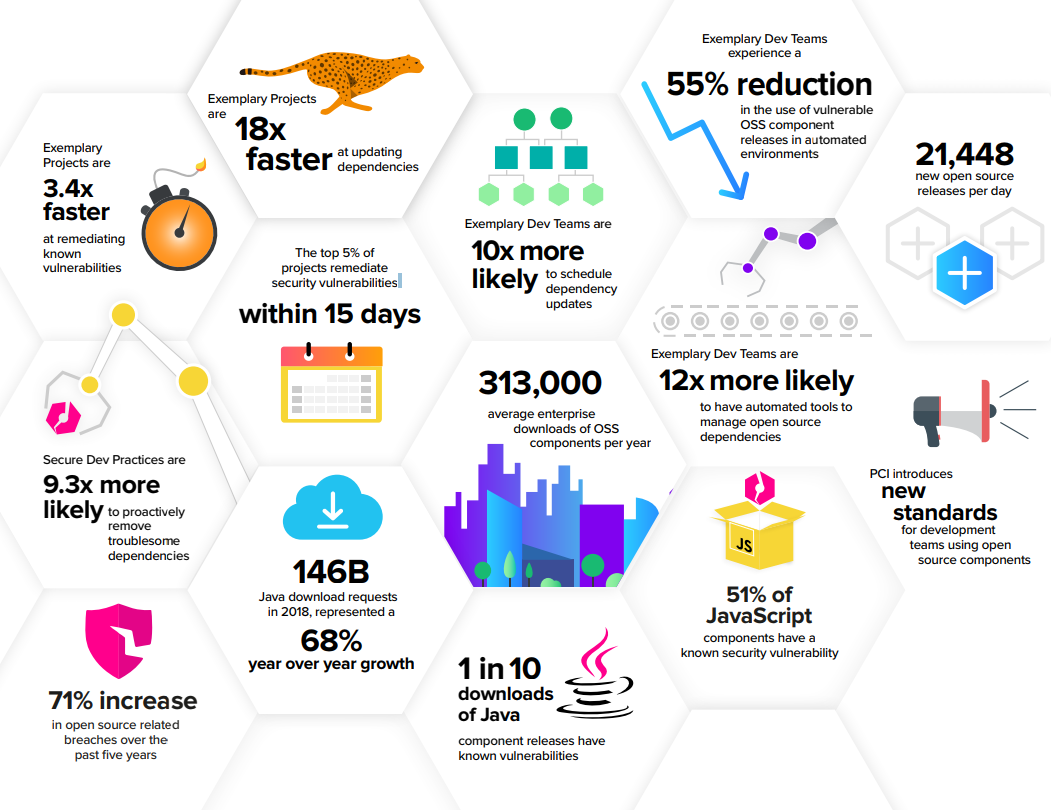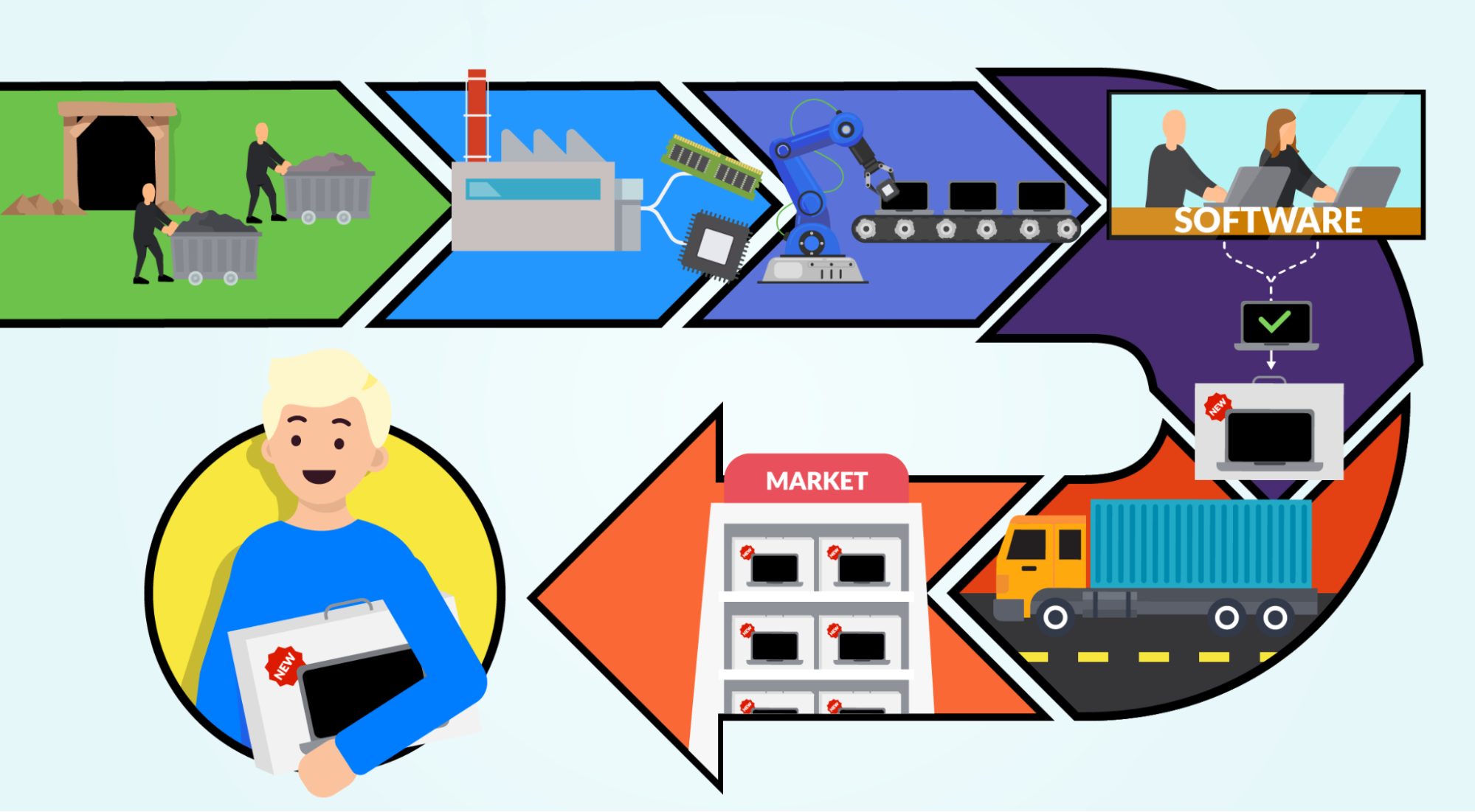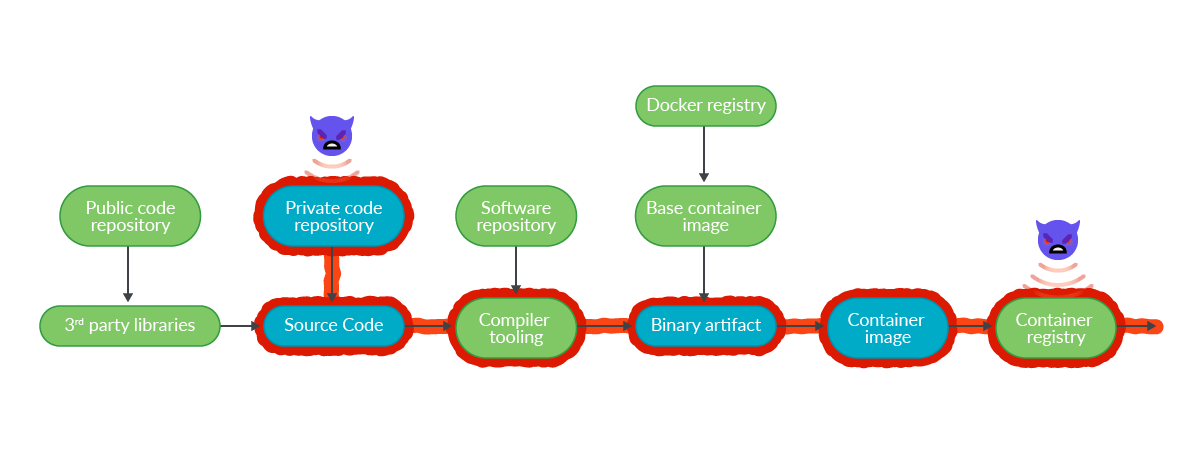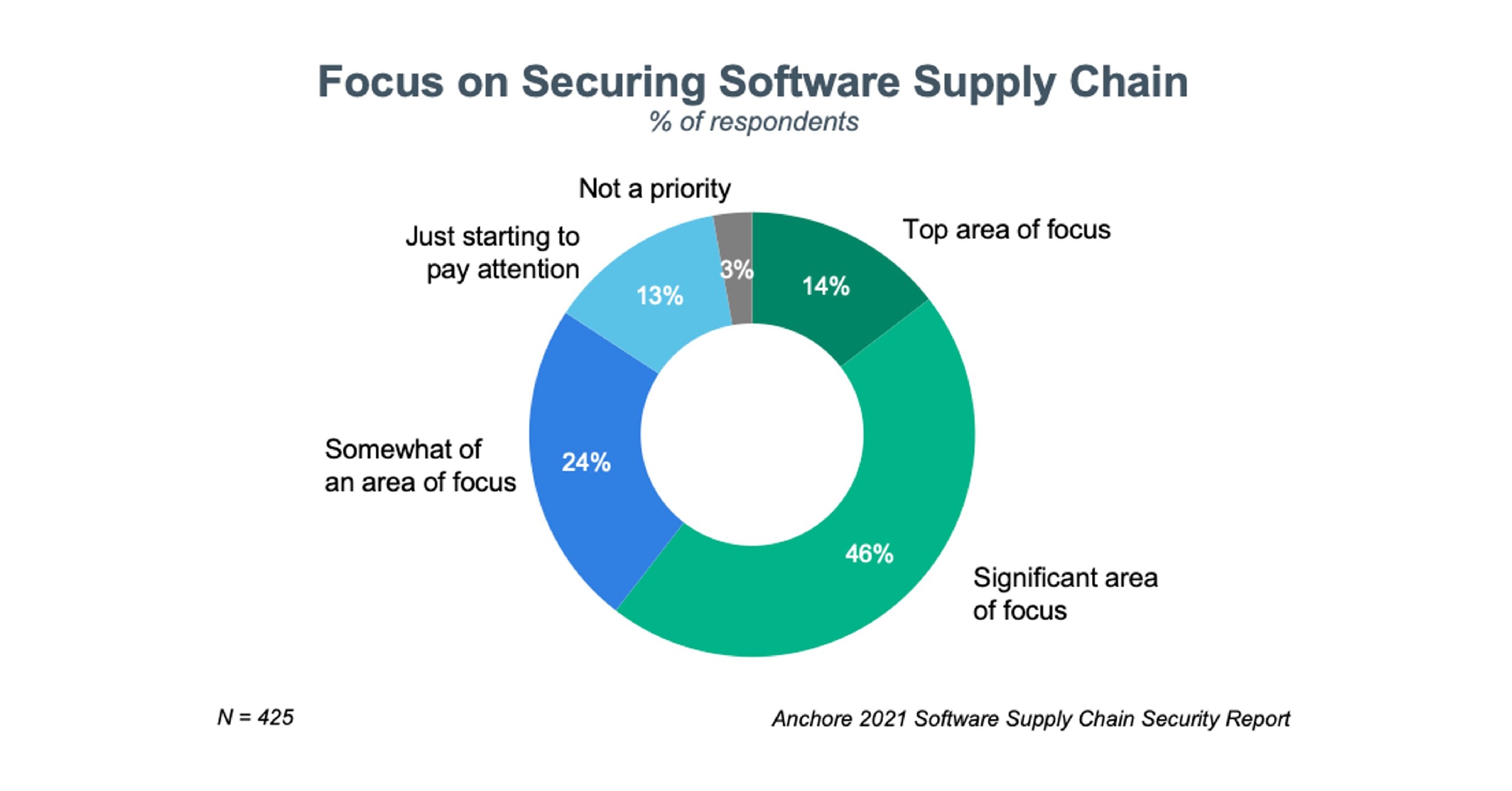
Survey of Large Enterprises Shows 64 Percent Affected by a Software Supply Chain Attack in the Last Year

How to Select the Best Supply Chain Management Software for Your Business in 2024 - Reviews, Features, Pricing, Comparison - PAT RESEARCH: B2B Reviews, Buying Guides & Best Practices