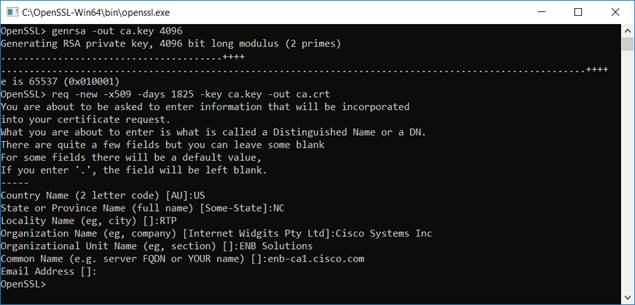
Design Zone for Branch/WAN - Cisco Catalyst SD-WAN Control Components Certificates and Authorized Serial Number File Prescriptive Deployment Guide - Cisco

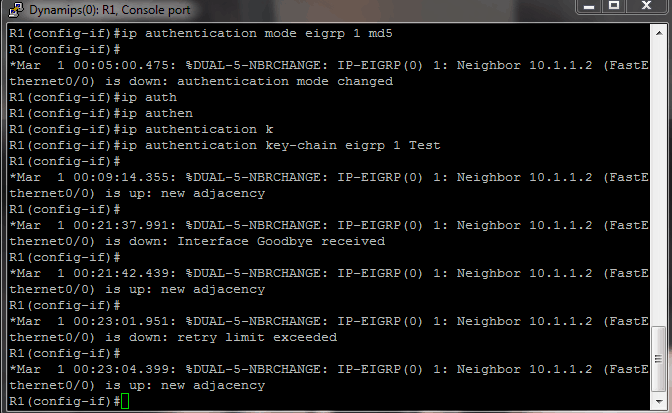
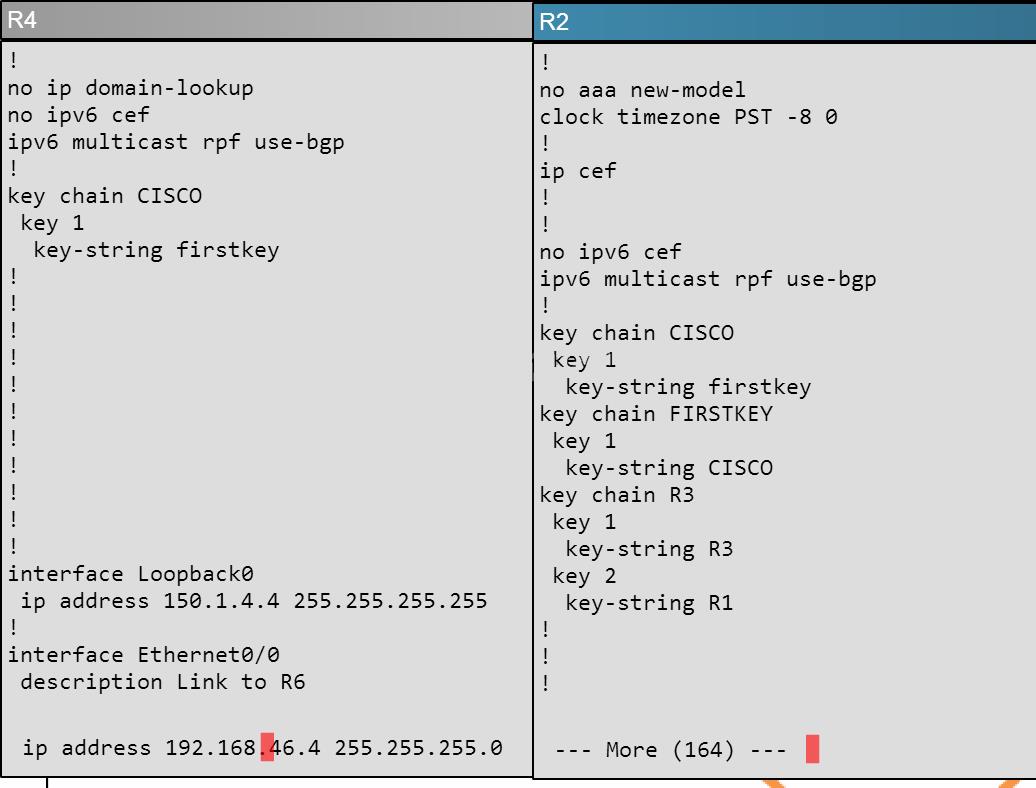
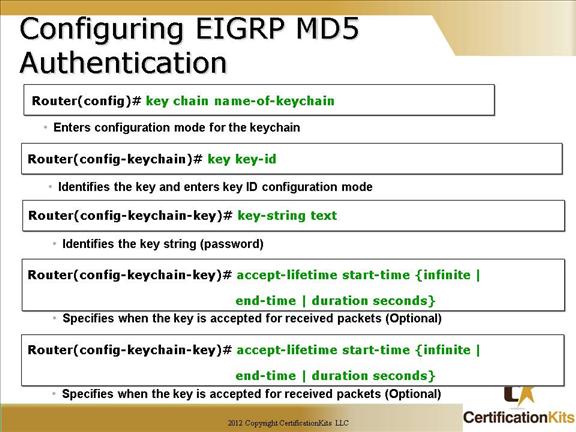
Which key chain is being used for authentication of EIGRP adjacency between R4 and R2? Answer in Here
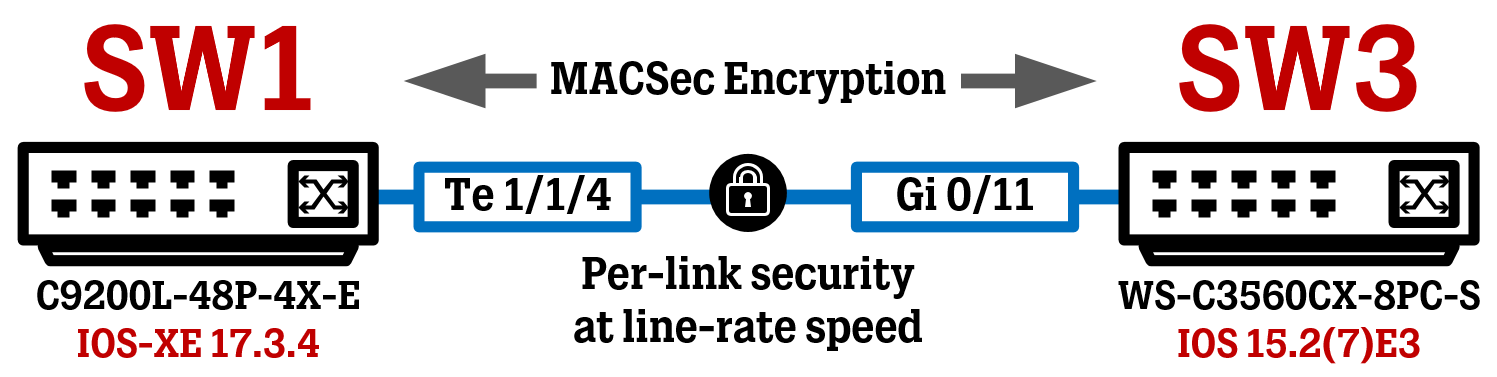
Cisco MACSec Switch-to-Switch Configuration using Pre-Shared Key between IOS-XE and IOS — WIRES AND WI.FI